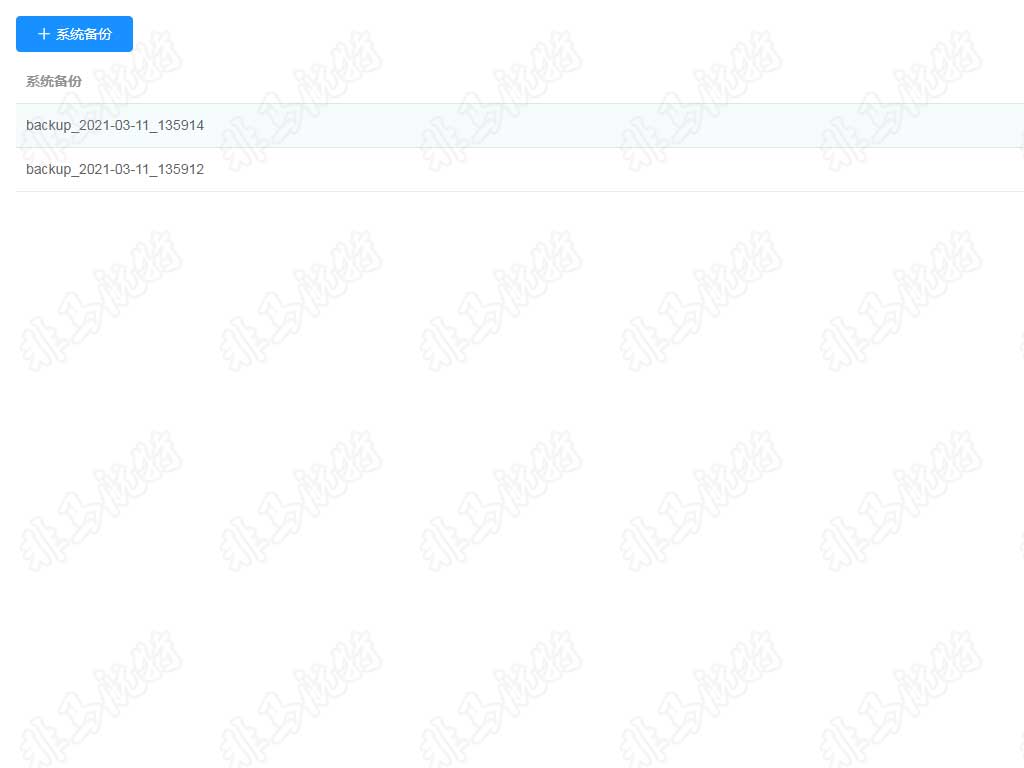
Customize User Permissions
The software uses role-based access control (RBAC) for enterprise security policy management. A user can have multiple roles, and each role has several operation permissions and one data permission. The superposition of all role permissions is a user's permission set.
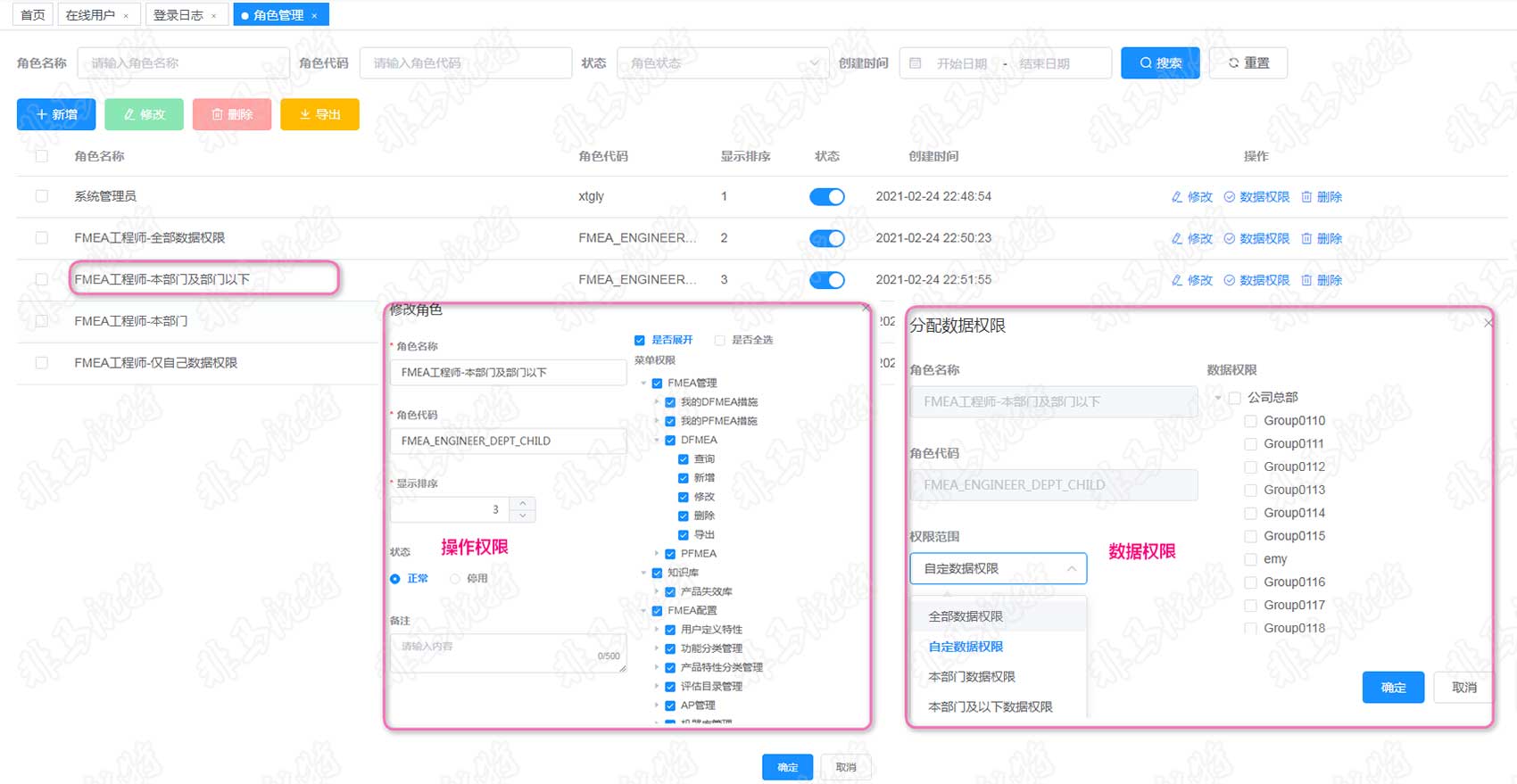
Audit Log
All operations of the system will automatically generate operation logs, which can be queried and used for auditing.
Abnormal Operation Record and Alarm
The user's abnormal operation will be recorded in the log for later viewing, and will prompt the user in time.
Data Backup
The software can customize the scope and frequency of data backup as required.